The folks over at Jamf found and analyzed a stealer built in Python, and compiled into a Mac app using PyInstaller. As they point out, it’s not new to see Mac malware using PyInstaller, but to their knowledge this is the first stealer to do so. Let’s take a look.
Python and macOS
Python malware is nothing new. Because macOS used to come with Python preinstalled, going all the way back to Mac OS X 10.2 (Jaguar), it was a popular language to use for a variety of things, malware included. However, as of macOS 12.3 (Monterey), Apple removed the outdated Python 2 from the system, and did not replace it with Python 3 (for licensing reasons, IIRC).
This was unfortunate for many Mac admins, researchers, etc, who had tools written in Python that would previously “just work” on any Mac. Thus PyInstaller gained popularity. It makes sense that malware developers would use it.
Malware behavior
The malware in question – a Mac executable file named “stl” – can be seen to do a variety of tasks using the shell to run osascript to run AppleScript commands. (One wonders why they didn’t simply write the malware in compiled AppleScript. 🤷♂️)
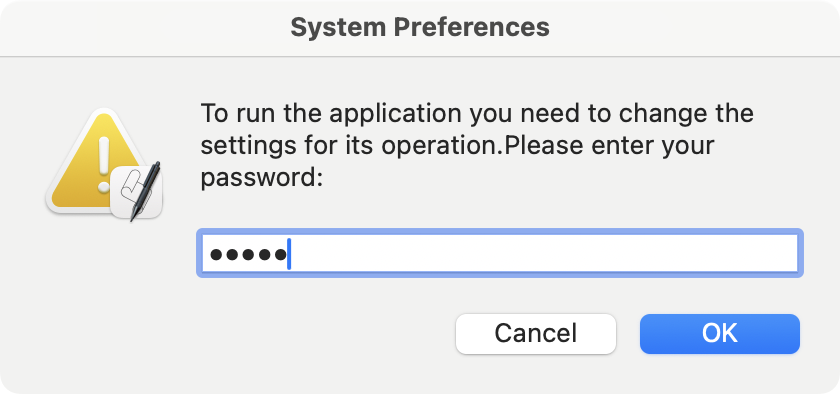
osascript -e display dialog 'To run the application you need to change the settings for its operation.Please enter your password:' with title 'System Preferences' with icon caution default answer '' giving up after 30 with hidden answer
This is pretty typical malicious AppleScript usage, triggering a dialog to display that appears to be a password prompt. It won’t exactly match a standard macOS dialog, but it will still fool some people.
dscl /Local/Default -authonly [user] [pass]
The above command, with a correct username inserted and the password entered in the fake dialog, is presumably used to determine whether the user input the correct password. Without testing this malware live, I would have to assume that it would continue to show the dialog until it got the correct password.
osascript -e do shell script 'tccutil reset AppleEvents'
This will cause the Mac to forget any decisions the user has made with regard to allowing AppleScripts to get information from other apps. (For example, you could write a script to get the subject and body of a message from Mail, and this would trigger a TCC alert asking for permission to do this.) If the user had already denied this permission, this would result in them being asked again… giving the malware a chance to get a more favorable answer.
osascript /tmp/osascr.scpt
This would run a presumably malicious script that was dropped in the temporary folder.
Ultimately, the malware has the capability to execute arbitrary payloads downloaded from an attacker-controlled server, collect keychain data, and capture cryptocurrency wallet data.
Malware construction
The analysis goes into quite a bit more detail as to how the PyInstaller-built binary works, where all the bits and pieces are stored in the binary, etc. I won’t repeat all that, as you’d be better off reading the original analysis.
I find it very interesting how much effort was put into obfuscation, between the use of PyInstaller (which includes only compiled Python files, not the original Python code) and other obfuscation and encryption techniques. This is particularly ironic given the use of AppleScript for some of the functionality. A compiled AppleScript app would be significantly more difficult to reverse engineer. Few people know how to reverse compiled AppleScript, and even for those who do, it takes a great deal of effort just to get a fairly high-level overview.
Is this a threat?
It’s hard to know if this is truly in the wild or if it’s a proof-of-concept, since Jamf’s researchers found it on VirusTotal. It’s not unheard of for malware developers to upload early versions of malware to VirusTotal to see if it’s detected by anything.
Interestingly, neither stl nor any of the extracted components are detected as malicious by any of the engines on VirusTotal. The only part that seems to be detected is a deobfuscated Python file created during Jamf’s analysis. So, if it is in the wild, it would be likely to evade detection by most antivirus at the moment.
IOCs
stl: fc95ff687cfd775acac3b0457332dca170e58b77b27f3ee4f9013984fd9b388d
